Cybersecurity awareness training's primary objective is to enhance our employee's and student's knowledge and understanding of potential cybersecurity risks and implement measures to protect themselves and their organization from cyber-attacks and data breaches.
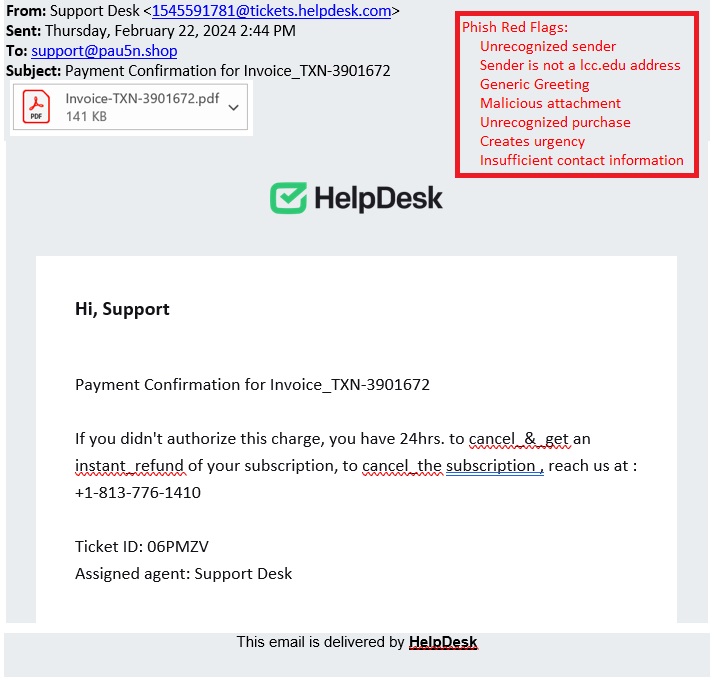
Phish Bowl
The phish bowl is a list of phishing (fake) emails that have been spotted at Lansing Community College. If you receive a suspicious email, send it to the LCC Help Desk at lcc1@lcc.edu for a review.

Safety Plan Podcasts
Director of Information Security Paul Schwartz presents on various cybersecurity scams and how to avoid them. Episodes include topics such as sextortion, malware, phishing, fake job scams, skimmers, QR code scams, and tax refund scams.
Videos

How to Identify a Phishing Email
Phishing occurs when criminals try to get us to open harmful links, emails or attachments that could request our personal information or infect our devices. Phishing messages or “bait” usually come in the form of an email, text, direct message on social media or phone call. These messages are often designed to look like they come from a trusted person or organization, to get us to respond. Watch this video to learn how to identify a phish email and avoid the scam.

How to Create a Password Manager
A password manager is a program that stores and manages passwords for online services and local applications. A complex password manager can generate passwords for all online accounts, automatically enter passwords into apps and websites, and store passwords in an encrypted database. Users re-use their passwords between websites and account because it’s difficult to remember lots of difference passwords. Watch this video to learn how to create a password manager so you can use unique passwords at every site.

How to Conduct a Confidential Information Scan
Confidential data scanning means using a software tool to examine the files stored on your computer to discover which files, if any, contain confidential data. Watch this video to scan your computer and email for confidential information.

How to Conduct an Antivirus Scan
Whether you think you might have a virus on your computer or devices, or just want to keep them running smoothly, it’s easy to do a virus scan. In this video, you will learn how to conduct an antivirus scan.

Teachable Moment
The President of LCC interviews the Director of Information Security on the biggest threat to LCC – Phishing. Falling for a malicious email could lead to a malware infection, credential theft, identity theft, reputation/branding/perception loss, and possibly a front-page news story of LCC's Big Data Breach. In the interview it is explained how to identify a fraudulent/phishing email.
Employee Computer Based Training
The LCC Information Security office has created a computer based training module called CSI-LCC: Computer Security Information on LCC's Talent Management System (LMS) (only available to LCC employees). Information security is important because it protects sensitive information from unauthorized activities like inspection, modification, recording, and disruption. It also helps to maintain the integrity and confidentiality of information, and block the access of hackers. The goal of information security is to ensure the safety and privacy of critical data, such as customer account details, financial data, or intellectual property. In this training, employees are instructed on their responsibilities to protect LCC information.
Resources
- Center for Cybersecurity Education
- Annual Verizon Data Breach Investigations Report
- SANS Institute
- National Institute of Standards and Technology (NIST)
- Center for Internet Security
- National Cybersecurity Alliance
- Virustotal
- Hybrid Analysis
- Internet Crime Complaint Center (IC3)
- Federal Bureau of Investigation
- Internal Revenue Service

Contact Us
Information Security
Technology and Learning Center, Room 421J
Phone: 517-483-5264
Fax: 517-483-1758
